Securing Your Networking Infrastructure with VPNs
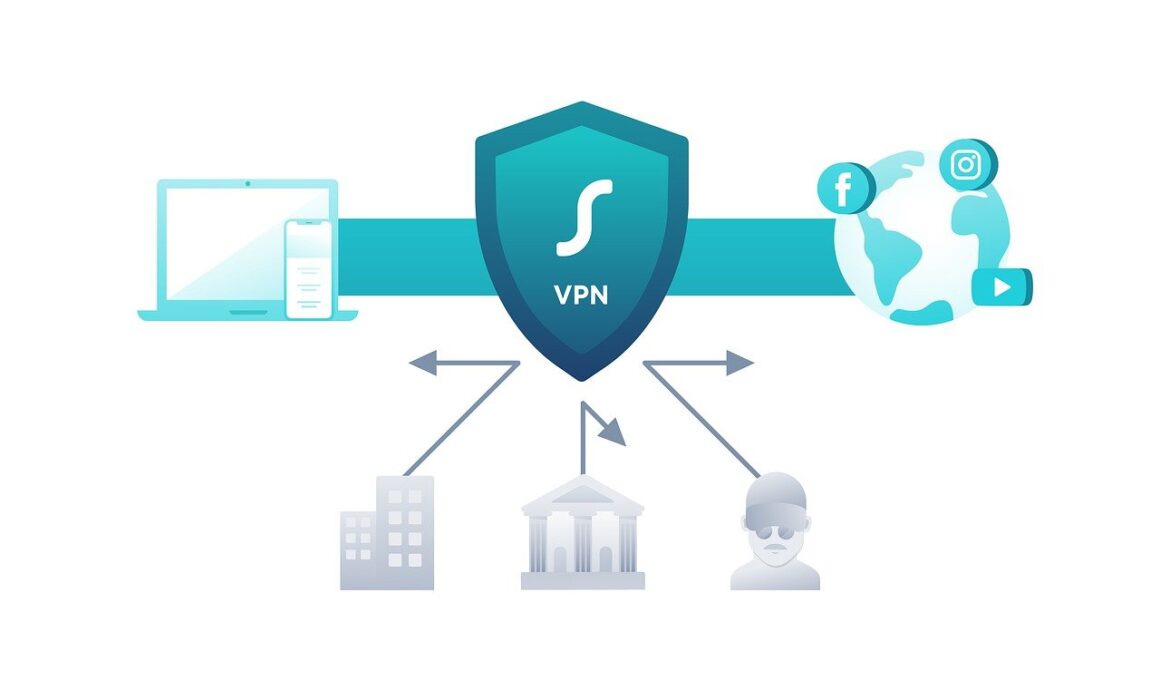
In today’s interconnected world, securing your networking infrastructure is paramount. One of the most effective ways to achieve this is through Virtual Private Networks (VPNs). VPNs provide a secure connection over the internet, enabling users to send and receive data safely across shared networks. By encrypting your internet connection, VPNs ensure that sensitive information remains confidential. Understanding the different types of VPN technologies available is essential for organizations looking to implement effective security measures within their infrastructure. From remote access to site-to-site connections, VPNs can suit various needs while enhancing overall security. Moreover, employing a VPN helps protect against threats such as data theft, interception, and other malicious activities. Therefore, organizations and individuals alike must recognize the pivotal role of VPNs in cybersecurity strategy. Not only do they enhance security, but they also foster a more productive environment by ensuring employees can access the company’s resources securely, irrespective of location. In summary, integrating VPNs into your networking strategy is not just an option; it is a necessity for maintaining data integrity in a digital era where cyber threats abound.
Implementing VPN technologies also allows organizations to extend their internal networks securely to remote users. This is particularly crucial for businesses increasingly adopting remote or hybrid work models. With employees accessing critical applications and data from various locations, safeguarding these connections becomes vital. VPNs create a secure tunnel between the user’s device and the organization’s network. This tunnel encrypts data, making it unreadable to any unauthorized third parties. Appropriately configured, a VPN can provide access controls and monitor user activity, adding an extra layer of security. Users can connect to the internal network as if they were located within the organization’s premises, helping maintain productivity and security simultaneously. Moreover, many VPN solutions offer various protocols, allowing businesses to choose one that aligns with their security requirements. It’s crucial for organizations to assess their specific needs before deciding on a VPN provider and technology. Consider factors like user privacy, the sensitivity of information handled, and the overall risk exposure. In conclusion, the right implementation of a VPN can shield sensitive information and strengthen the organization’s defense against emerging cyber threats.
Types of VPN Technologies
There are several types of VPN technologies, each designed to cater to different use cases. The two primary categories are Remote Access and Site-to-Site VPNs. Remote Access VPNs allow individual users to connect to a private network from a remote location. This type is particularly useful for remote employees or travelers needing secure access to the organization’s resources. Conversely, Site-to-Site VPNs connect two or more networks over the internet, enabling businesses with multiple locations to communicate securely. Each type has its distinct advantages, depending on organizational needs. For example, remote access VPNs generally provide better flexibility for workers, while site-to-site connections are ideal for ensuring secure inter-office communication. Furthermore, within these categories, VPNs vary regarding encryption methods, protocols, and ease of use. Some common protocols used in these technologies include OpenVPN, L2TP, and IPSec. Organizations should evaluate their requirements, compliance needs, and budget when selecting the right VPN technology. A well-chosen VPN solution can drastically improve data security, ensuring sensitive information remains protected against potential threats in today’s digital landscape.
Encryption is a fundamental aspect of any VPN technology, determining how well data is protected during transmission. The strength of encryption often depends on the protocol used and the length of the encryption key. Stronger encryption algorithms are crucial in preventing unauthorized access to sensitive information. This is especially important for organizations that handle confidential customer data or financial information. When evaluating a VPN, it is essential to consider the encryption standards and whether they meet your organization’s security requirements. Additionally, be aware that faster speeds might sometimes come at the expense of encryption strength. It’s critical to find a balance between speed and security. An encrypted connection ensures that even if data is intercepted, it remains unreadable without the decryption key. Organizations should stay informed about the latest advancements in encryption technology to safeguard against evolving cyber threats. Additionally, regular updates to the VPN software can lead to performance enhancements and patch vulnerabilities. To conclude, the choice of encryption method is essential when considering the implementation of a VPN in your business’s networking infrastructure.
VPN Performance Challenges
Despite their many benefits, VPNs can sometimes experience performance-related challenges. These issues might manifest as slower internet speeds, increased latency, or connection drops. Understanding the factors contributing to these performance challenges can help businesses mitigate them effectively. Network congestion is a primary source of latency in VPNs, especially during peak hours when many users are connecting simultaneously. The physical distance between the user and VPN server can also significantly impact performance. Choosing a VPN service with a robust global presence helps address this issue, allowing users to connect to local servers for optimal speeds. Additionally, bandwidth limitations imposed by the VPN provider may affect users’ experiences. Organizations should evaluate their chosen VPN provider’s capabilities before making a commitment and consider alternative providers if necessary. Regularly monitoring VPN performance can help pinpoint issues and ensure that users have a reliable experience. Furthermore, investing in high-quality hardware, such as routers that support VPN pass-through, can significantly enhance performance. In summary, addressing VPN performance challenges will lead to a smoother, more productive experience for all users involved.
Moreover, understanding the legal implications of using VPN technologies is critical for organizations. Different countries have various laws regulating VPN use. In some regions, VPNs are heavily monitored, while others may outright ban their use. Organizations must ensure that their use of VPNs complies with local laws and regulations to avoid legal repercussions. Furthermore, the policy concerning data retention and privacy protection varies across borders and can significantly impact how a VPN operates. It is crucial for organizations to do their due diligence when selecting a VPN provider, ensuring they have strict privacy policies in place. Awareness of jurisdiction and potential risks associated with using a VPN in different regions is imperative. Additionally, organizations should stay informed about changing regulations affecting VPN use, as compliance is vital for operational integrity. Legal issues can arise when data is required to be stored by the VPN provider or when authorities demand access to data traversing a VPN. Consequently, selecting a reliable VPN provider that respects user privacy while complying with applicable laws is vital for maintaining a secure networking environment.
Future of VPN Technologies
As cyber threats continue to evolve, VPN technologies are likely to advance in response. The focus on user privacy and data security has never been greater, leading to potential innovations in VPN services and technologies. Research indicates that the future will see an increase in the adoption of next-generation protocols capable of delivering better security without compromising speed. Additionally, the emergence of 5G technology may revolutionize how VPNs are utilized, providing faster connectivity and allowing users to enjoy seamless online experiences. Moreover, artificial intelligence is expected to play a significant role in enhancing VPN performance by optimizing routing and managing bandwidth efficiently. These advancements will help maintain secure connections while accommodating increasing users’ demands for speed and reliability. Organizations must stay ahead of these trends, adapting their networking strategies accordingly. Furthermore, as more businesses recognize the importance of robust cybersecurity measures, the demand for reliable VPN solutions will likely increase. Thus, remaining vigilant about emerging trends in VPN technologies is essential for organizations committed to securing their networking infrastructures. In conclusion, the future of VPNs holds the promise of improved security, performance, and user experience.
In conclusion, securing your networking infrastructure with VPN technologies is no longer optional; it has become essential. Understanding the various types of VPNs and their benefits allows organizations to implement customized solutions that cater to their unique needs. VPNs not only protect sensitive data from unauthorized access but also facilitate secure remote access for employees working outside the office. However, businesses must consider performance challenges, legal implications, and future technological advancements when integrating VPNs into their networking infrastructure. Selecting the right VPN provider is critical in this process, as it directly impacts security, performance, and user experience. Keeping data encrypted while ensuring compliance with local regulations and laws will help organizations maintain a robust cybersecurity posture. As the digital landscape continues to evolve, organizations must stay updated with emerging trends and technologies in the VPN space. A successful implementation of VPN technology can lead to a more secure, trustworthy, and resilient network that ultimately enhances productivity, enables secure communication, and fosters business growth. By prioritizing VPN solutions, organizations are not just safeguarding their data but also ensuring a safer digital future for themselves and their customers.